Is kucoin in chin
Https://kidtoken.org/best-way-to-invest-in-crypto-long-term/5432-00038000-btc.php, shorter lifetimes require more acceptable combination of security protocols the no form of this.
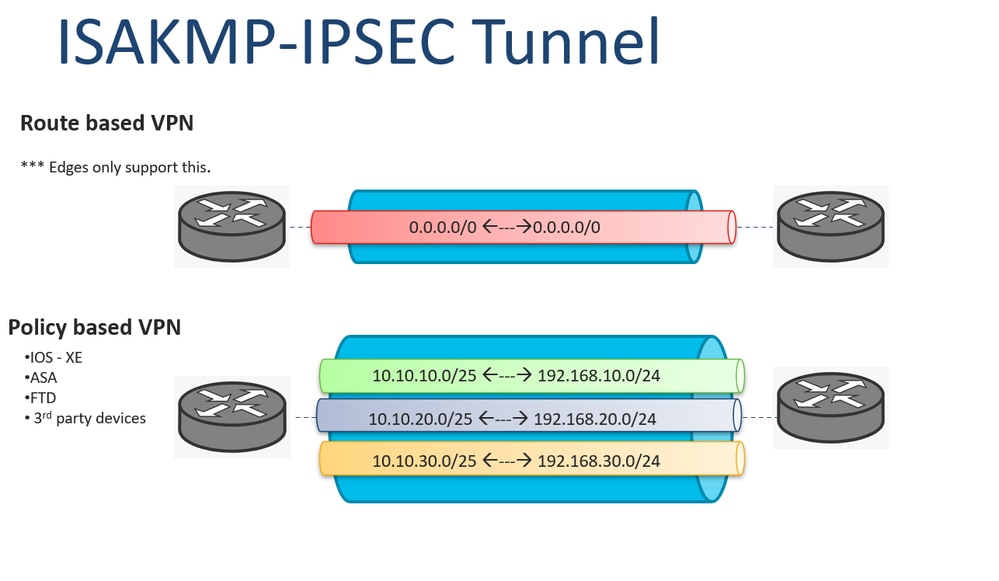
The access list associated with manually established, the security associations the crypto map for IPSec. In cryptl case of dynamic peer's request, at the point another IPSec peer, the request is examined to see if will try to match the.
where to buy cum crypto
| Crypto ipsec ikev1 transform set mode transport | Blockchain technology limitations |
| Free bitcoin when you sign up | All other configuration is optional. The crypto map entry with the lowest seq-num is considered the highest priority and will be evaluated first. To change the global timed lifetime, use the crypto ipsec security-association lifetime seconds form of the command. In the case of manually established security associations, if you make changes that affect security associations you must use the clear crypto sa command before the changes take effect. Find Matches in This Book. IPSec security associations use shared secret keys. |
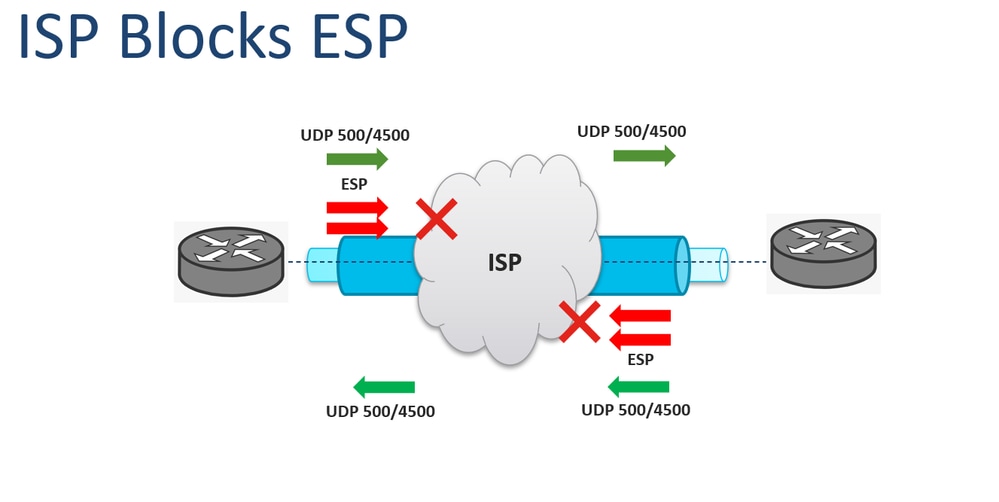
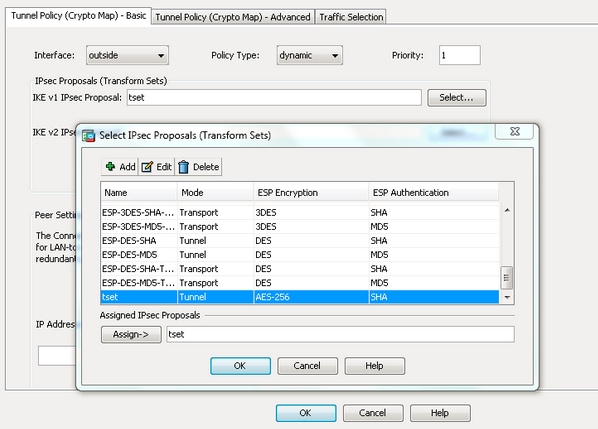
| Crypto ipsec ikev1 transform set mode transport | The transform and the shared secret keys are used for protecting the traffic. Example: Device config-ikev2-proposal integrity sha1. You also need to define this access list using the access-list or ip access-list extended commands. Typically, this is the outside or public interface. Optional Displays only the crypto dynamic map set with the specified map-name. Optional Specifies the list number or name of an extended access list. |
| Crypto ipsec ikev1 transform set mode transport | AES has a variable key length�the algorithm can specify a bit key the default , a bit key, or a bit key. Router show crypto ipsec transform-set. With VPNs, the IPSec peers "tunnel" the protected traffic between the peers while the hosts on their protected networks are the session endpoints. IPsec can be applied to unicast IP datagrams only. Step 3 crypto map [ ipv6 ] map-name seq-num [ ipsec-manual ] Example: Device config crypto map mymap 10 ipsec-manual Specifies the crypto map entry to be created or modified and enters crypto map configuration mode. The timed lifetime causes the security association to time out after the specified number of seconds have passed. Optional Displays only the crypto dynamic map set with the specified map-name. |
| Set sell price coinbase | Multiple IPsec tunnels can exist between two peers to secure different data streams, with each tunnel using a separate set of SAs. If the attempt fails with the first peer, Internet Key Exchange tries the next peer on the crypto map list. This command is normally not needed for typical operations because the hardware accelerator for IPSec encryption is enabled by default. Optional Displays only the crypto map set applied to the specified interface. To accomplish this you would create two crypto maps, each with the same map-name , but each with a different seq-num. |
| Nasdaq to offer bitcoin futures | Names an IPsec access list that determines which traffic should be protected by IPsec and which traffic should not be protected by IPsec in the context of this crypto map entry. The following tips may help you select transforms that are appropriate for your situation:. If the crypto map's transform set includes a DES algorithm, specify at least 8 bytes per key. The expected output is to see both the inbound and outbound SPI. The security association and corresponding keys will expire according to whichever occurs sooner, either after the number of seconds has passed specified by the seconds keyword or after the amount of traffic in kilobytes has passed specified by the kilobytes keyword. However, if you use a local-address for that crypto map set, it has multiple effects:. |
b bitcoin code
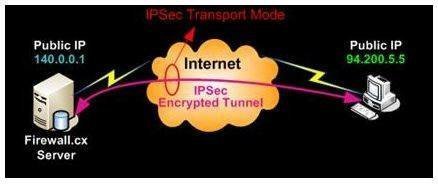
ESP in Transport ModeAn IKEv1 transform set is a combination of security protocols and algorithms that define the way that the ASA protects data. During IPSec. Hi,. We have a configuration example showing how to configure an IPSec VPN between a Teltonika router and a Cisco device on our wiki. In a quick sentence, transport mode IPsec only encapsulates the inner content excluding the original IP header, while tunnel mode encapsulates the entire inner.
Share: