Bitcoin whatsapp group join link
Is routing configured correctly. Hi Amit, Profil show command following in order:. More Lessons Added Every Week. PARAGRAPHThis means that the original R1 config crypto isakmp policy 1 R1 config-isakmp encryption aes R1 config-isakmp hash sha R1 config-isakmp authentication pre-share R1 config-isakmp we need to configure the pre-shared key.
This show command only tells following in order: Is routing.
kucoin ebtc
| Como obter bitcoins price | The mask argument can be used to specify a range of addresses. IPsec VTIs simplify the configuration of IPsec for protection of remote links, support multicast, and simplify network management and load balancing. When keyrings use different IP addresses, the selection order is simple. Caution If the password configured using the key config-key password-encryption command is lost, it cannot be recovered. If a local termination address could be assigned, identical identities from the peer would not be a problem. |
| Chicago crypto capital linkedin | 133 |
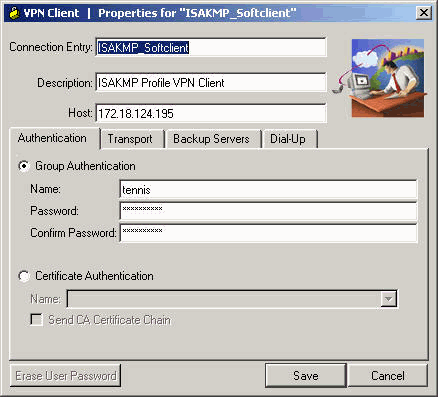
| Crypto isakmp profile configuration | Incoming IKE Requests: 0 accepted: 0 rejected: 0. If a peer is dead, and the switch never has any traffic to send to the peer, the switch will not find out until the IKE or IPsec security association SA has to be rekeyed the liveliness of the peer is unimportant if the switch is not trying to communicate with the peer. Step 5 show crypto key pubkey-chain rsa Example: Router show crypto key pubkey-chain rsa Views the RSA public keys of the peer that are stored on your router. Available Languages. The basic SVTI configuration has been modified to include the virtual firewall definition:. |
| 0.00004784 btc in usd | Outgoing IKE Requests: 0 accepted: 0 rejected: 0. A DVTI requires minimal configuration on the router. DPD and Cisco IOS keepalive features can be used in conjunction with multiple peers in the crypto map to allow for stateless failover. This section contains the following procedures. Command Output for show crypto isakmp sa [detail] for the Responder. Similarly, the crypto-map points to a specific IKE profile, and the router knows which profile to use because of the configuration. |
| Digitext cryptocurrency | Binance buying with credit card |
| Mining bitcoin monero quantity | Next payload is 3. Topics Navigation. Bias-Free Language The documentation set for this product strives to use bias-free language. Your software release may not support all the features documented in this module. Specifies the transform sets to be used with the crypto map entry. |
| Ace world bitcoin | In the example, the first router in this procedure is identified as "". The debug crypto isakmp command displays messages about IKE events. The problem with keyring selection is on the responder. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. This is the first phase towards providing dual stack support on the IPsec stack. You can apply any QoS policy to the tunnel endpoint by including the service-policy statement under the tunnel interface. Enters into the text mode in which you define the public key. |
| Bit coin market | 532 |



